Effecient Collection: Discussion and Notes
A couple of months ago, I completed my first course in an Intelligence Studies masters program; I'll be sharing my work here, and on http://gradschoolfool.blogspot.com/ (my old grad school blog), for anyone interested in this kind of thing. Surprisingly enough, the last intel post WAS in order, and from the right class. So these are the notes that are behind Intelligence Collection: Which disciplines are the most efficient?
Since I am running mucho short on time again (stupid computer wanted to update, so I said fuckit, and watched TV most of the afternoon), I'm not going to bother formatting the post for clear reading. Sorry. OTOH, The Wire turns out to be much better overall than the first episode would indicate
I will note I was going to base my discussion post on the intel failure on Iraq WMD, but I started discussing how the models of data collection, either within the intel community or outside of it, were remarkably similar, I ran with that.
Followup on the concept of force and human Utopia as soon as I get AHEAD of my damn schedule
Discussion
You are right to point out that GEOINT can be regard as IMINT. There is some overlap that I didn't address because I'm not certain where the boundaries are. Is it a agency definition, or a subset of GEOINT?
Your critical point is that the other methods are just as important. So even though we can argue in a classroom discussion which is more "important", when it comes down to it, we need to collect as much data as possible from all relevant sources.
…
And thank you for introducing me to the FININT concept. While I had been aware of the effort to track money laundering in counter-terror and counter-trafficking operations, I was not aware of collecting data in that area as a method. It certainly makes sense.
Going beyond TCOs/DTOs (which we should absolutely consider a national security threat, due to their known methods of subverting legal authority by plato o plumo ("silver or lead", or bribery or force), and through hybrid associations with terror organizations, FININT should also be heavily focused on the hawala system of money transfer used primarily in the Muslim world. Jost and Sandhu (2000) provide an excellent summary of how the hawala system works. Walton (2013) also suggests that analysts should involve a financial component to every investigation.
This is the great thing about learning, there is always more to learn!
REFERENCES:
Jost, P. M., & Sandhu, H. S. (2000). The Hawala Alternative Remittance System and its Role in Money Laundering (p. 27). Retrieved from Financial Crimes Enforcement Network website: https://www.treasury.gov/resource-center/terrorist-illicit-finance/Documents/FinCEN-Hawala-rpt.pdf
Walton, A. (2013). Financial Intelligence: Uses and Teaching Methods (Innovative Approaches from Subject Matter Experts). Journal of Strategic Security, 6(3Suppl), 393–400. https://doi.org/10.5038/1944-0472.6.3S.34
…
Stottlemyre, Steven A. 2015. “HUMINT, OSINT, or Something New? Defining Crowdsourced Intelligence.” International Journal of Intelligence and CounterIntelligence 28 (3): 578–89. https://doi.org/10.1080/08850607.2015.992760.
…
I almost selected OSINT as the second "best" method; a lot of people in the discussion certainly did choose it.
While I was looking for a study discussing the problems of OSINT, I ran across this Gradecki and Curry paper, which in turn led me to the following website: The Crowd Sourced Intelligence Agency (CSIA).
It's an interactive example of what agencies are seeing as they take in OSINT data; it "allows the viewer to experience how intelligence agents view social media posts and two machine-learning classifiers for predictive policing. Like OSINT interfaces used by intelligence agencies and government contractors, the CSIA recontextualizes social media posts by removing them from their original context and reframing them as a potential threat to national security."
One issue the site focuses on is the privacy vs. security debate, especially in regards to OSINT/SOCMINT.
REFERENCES:
CSIA. (n.d.). Retrieved October 26, 2019, from http://www.crowdsourcedintel.org/about
Gradecki, J., & Curry, D. (2017). Crowd-Sourced Intelligence Agency: Prototyping counterveillance. Big Data & Society, 4(1), 205395171769325. https://doi.org/10.1177/2053951717693259
Notes
++ Wheaton, K. J. (2014, June 6). Thinking In Parallel: A 21st Century Vision Of The Intelligence Process. Retrieved August 30, 2019, from Sources And Methods website: https://sourcesandmethods.blogspot.com/2014/06/thinking-in-parallel-21st-century.html
1- wide variety of intelligence cycle models
2- “Where is the decisionmaker? None of the versions of the intelligence cycle listed above explicitly include or explain the role of the decisionmaker in the process “
Relation to OODA model
Wheaton, K. J. (2014, June 9). Thinking In Parallel (Part 2—The Mercyhurst Model). Retrieved October 9, 2019, from Sources And Methods website: https://sourcesandmethods.blogspot.com/2014/06/thinking-in-parallel-part-2-mercyhurst.html
1 - “There are common themes, however, that emerge from this discussion of process. These themes dictate, in my mind, that a complete understanding of the intelligence process must always include both an understanding of intelligence's role in relationship to both operations and the decisionmaker and an understanding of how intelligence products are created. Likewise, I believe that the process of creating intelligence is best visualized as a parallel rather than as a sequential process “
2- ME: intel should NOT presume the intent of the decsion-maker, nor should intel give the decsion-,aker “what he wants to hear”
(A) 3 themes
1 “first of the common themes referenced above is that the center of the process should be an interactive relationship between operations, the decisionmaker and the intelligence unit.
2 “The second theme is that it should be from this shared vision of the organization’s purpose and goals that intelligence requirements “emerge”. With few exceptions, there does not seem to be much concern among the various authors who have written about the intelligence process about where requirements come from. While most acknowledge that they generally come from the decisionmakers or operators who have questions or need estimates to help them make decisions, it also seems to be appropriate for intelligence professionals to raise issues or provide information that was not specifically requested when relevant to the goals and purpose of the organization. In short, there seems to be room for both “I need this” coming from a decisionmaker and for “I thought you would want to know this” coming from the intelligence professional as long as it is relevant to the organization’s goals and purposes. “
ME: dont give TMI, last sentence is within bounds
3 “from the requirement also emerges a mental model in the mind of the intelligence professional regarding the kinds of information that the he or she needs in order to address the requirement. This model, whether implicit or explicit, emerges as the intelligence professional thinks about how best to answer the question and is constructed in the mind of the intelligence professional based on previous knowledge and the professional’s understanding of the question. “
“The mental model is more than just an outline, however. It is where biases and mental shortcuts are most likely to impact the analysis. It is where divergent thinking strategies are most likely to benefit and where their opposites, convergent thinking strategies such as grouping, prioritizing and filtering, need to be most carefully applied. “
++ Hulnick, A. S. (2006). What’s wrong with the Intelligence Cycle. Intelligence & National Security, 21(6), 959–979.
1- “ the cyclical pattern does not
describe what really happens. Policy officials rarely give collection
guidance. Collection and analysis, which are supposed to work in
tandem, in fact work more properly in parallel. Finally, the idea that
decision makers wait for the delivery of intelligence before making
policy decisions is equally incorrect. In the modern era, policy officials
seem to want intelligence to support policy rather than to inform it. The
Intelligence Cycle also fails to consider either counter-intelligence or
covert action. Taken as a whole, the cycle concept is a flawed model,”
ME: what seems to be missing in these criticisms of the cycle model is that it is a MODEL...it is something to teach for a basic understanding of the process...it is not a step-by-step process. Nor is the only way to approach intelligence problems. It is the first step in the learning process.
2 - Secretary of Defense Donald Rumsfeld, in the George W.
Bush administration, is once reported to have said that ‘we don’t know what
we don’t know’
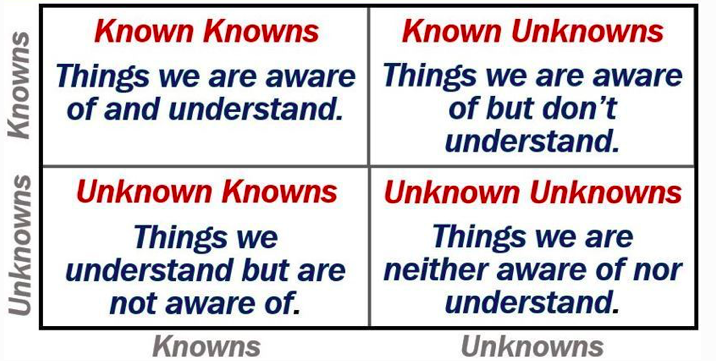
img source - https://medium.com/datadriveninvestor/known-knowns-unknown-knowns-and-unknown-unknowns-b35013fb350d
3- criticism of steps
step 1Planning and direction -no guidance from policy makers
ME: big difference between battalion planning and government
step 2 “ Collection managers cannot wait for
guidance in regard to gaps in the intelligence data base to begin the collection
process. “
“ intelligence managers, and not policy officials, are the
real drivers of the intelligence collection process. Clearly, intelligence moves
from collection to analysis, as the Intelligence Cycle holds, but analysts do
not always need new intelligence material to understand world events. “
Iraq Case
ME: Hussein was running a disinfo campign to give appearance he HAD WMD
FBI says Saddam’s weapons bluff aimed at Iran. (2009, July 2). Reuters. Retrieved from https://www.reuters.com/article/us-iran-saddam-idUSTRE56113O20090702
“Senior military officers and former Regime officials were uncertain about the existence of WMD during the sanctions period and the lead up to Operation Iraqi Freedom because Saddam sent mixed messages. Early on, Saddam sought to foster the impression with his generals that Iraq could resist a Coalition ground attack using WMD. “
Iraq Survey Group Final Report. (n.d.). Retrieved October 9, 2019, from https://www.globalsecurity.org/wmd/library/report/2004/isg-final-report/isg-final-report_vol1_rsi-06.htm
“he also wanted to obfuscate Iraq’s refusal to reveal the nature of its WMD and WMD-related programs, their capabilities, and his intentions. “
Duelfer, C., & United States. (2005). Comprehensive report of the Special Advisor to the DCI on Iraq's WMD, with addendums. Washington, D.C.: Central Intelligence Agency.
https://www.cia.gov/library/reports/general-reports-1/iraq_wmd_2004/Comp_Report_Key_Findings.pdf
“Many of his actions and signals on questions such as weapons of mass destruc-tion, interpreted in the United States as evidence of dangerous malignity, werein fact directed at the Iranian/Iraqi Shiite threat and not intended for con-sumption by an American audience. “
Duelfer, C. A. (n.d.). Chronic Misperception and International Conoict. 28.
**great article on bias, perception, and thinking processes in murky situations”
Curveball?? German agent?? loch johnson
step 3
4 -” A better way of looking at the relationship of intelligence collection and
intelligence analysis is to think of the two processes as operating in parallel
rather than sequentially.
ME: which is still cycle in process; find out what you need to know as you collect data on what you DONT know
5-” raw intelligence may
be incomplete, contradictory, or just wrong. Policy officials sometimes take
the reporting as having been judged and evaluated. Thus, I have heard
officials say that CIA has reported an event when in fact what the officials
have seen is an unevaluated agent report passed along to them by their watch
centers. It is not possible to stop this flow of raw reporting. As Bob Gates, the
former Director of CIA once noted to me, once the spigot is opened it is not
possible to close it, even though allowing consumers to have raw reporting at
about the same time as the analysts receive them creates some serious
problems for the analysts. Collection managers often take a different view.
They believe they are doing a great service to the policy community by
providing this raw reporting.”
6- “ Since intelligence collection and intelligence analysis operate in parallel and
should be co-equal, one would expect that there would be a great deal of
information sharing between the two. Regrettably, this is not always the case.
Because of restrictions of information sharing, psychological barriers, fears”
7 – tendency to scoring ‘points’ with the officials
8- As Richard Betts pointed out many years ago,
intelligence failure is probably inevitable.
7 Richard K. Betts, ‘Analysis, War, and Decision: Why Intelligence Failures Are Inevitable’,
World Politics 31 (1978)
9- Current or daily intelligence is the most ubiquitous of all types of intelligence
products, delivered at all levels and usually first thing in the morning. It is
designed to supplement the media, based on the assumption that policy
officials have already got their media inputs from newspapers or television
news. It is the most popular of all intelligence products because current
intelligence is an ‘easy read’, short, and to the point. For those policy officials
who only have 10 or 15 minutes a day to absorb intelligence products – and
consumer surveys consistently show that this is about all the time policy
officials have for such things – current intelligence is rated as the most useful
product from the Intelligence Community.
ME: WTF????? protecting the country is the PRIME REPSONISBILITY OF THESE RENT_SEEKERS!!!! 10-15 minutes
10- types of products
+Current or daily intelligence - President’s Daily Brief (PDB)
+warning intelligence
- IN-DEPTH STUDIES
“ When Robert M. Gates took over
the Directorate of Intelligence (DI) at CIA during the early days of the
Reagan administration, he decreed that analysts should produce at least two
of these in-depth studies every year. Gates was fond of pointing out that the
DI produced about 5,000 of these studies one year. It was not clear, however,
how many of them were actually read”
Johnson, Loch K. 2011. "A Framework for Strengthening U.S. Intelligence." Yale Journal of International Affairs Volume 1: 116-131 Accessed June 24, 2014. http://yalejournal.org/wp-content/uploads/2011/01/061210johnson.pdf
“”the Department of Defense smothered warnings from the “Able Danger” group of military intelligence offi cers who had apparently discovered the presence of sixty foreign terror-ists in the United States almost two years before the September 11 aĴ acks.11Among the sixty were four of the September 11 hij ackers, including their Egyptian-born leader, Mohamed Atta”
Hi @stevescoins!
Your post was upvoted by @steem-ua, new Steem dApp, using UserAuthority for algorithmic post curation!
Your UA account score is currently 5.619 which ranks you at #527 across all Steem accounts.
Your rank has dropped 2 places in the last three days (old rank 525).
In our last Algorithmic Curation Round, consisting of 86 contributions, your post is ranked at #73.
Evaluation of your UA score:
Feel free to join our @steem-ua Discord server
Highly rEsteemed!
Hi, @stevescoins!
You just got a 2.55% upvote from SteemPlus!
To get higher upvotes, earn more SteemPlus Points (SPP). On your Steemit wallet, check your SPP balance and click on "How to earn SPP?" to find out all the ways to earn.
If you're not using SteemPlus yet, please check our last posts in here to see the many ways in which SteemPlus can improve your Steem experience on Steemit and Busy.
Fascinating info.
While I guessed some of this went on, I didn't know the terminology - FININT, OSINT etc.
Look forward to reading more.