Hive account theft or hacking

Lately we have been reading about more account thefts (what some consider hacking), which seems to indicate an increase in this criminal activity that affects many areas of the network, but that we can now see frequently in Hive.
I had written in Spanish about this topic, but I did not imagine the great impact that the post was going to have because of its informative and educational nature. So after several days I have decided to make this version in English to make my contribution about some security measures that can prevent you from having the hard time of seeing how someone takes over your account, starts to make Power Down and then, weekly is taking those funds, first to another account on Hive and then to some exchange, where we finally lose track of it definitively.
As a community leader, I have already seen and attended several cases and it is really sad to see, as in the case of my friend @partitura, who came to have more than 100 thousand HP and weekly now sees his money moving from one account to another, until it disappears, without him being able to do anything about it.
But how do they manage to take over our accounts?
Here the predominant factor is still the well-known "phishing". That is to say, by any means they send us a link that should take us to a Hive site, but when we get to the site we are surprisingly told to log in. The interface where you enter your username and password is exactly the same as Hive.blog, Peakd.com, Ecency.com or any other (which may include tribes such as Palnet.io, MusicForLife.io, LeoFinance.io, etc).
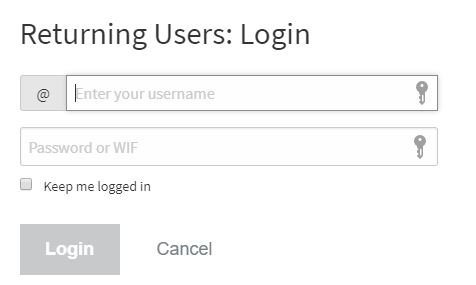
But, although the appearance is identical, what is going to be different is the web address, i.e. the URL. That's where we can see if we are on the site we intend or not. The sites used for phishing or data theft, look the same as the one that pretends to make us believe, but the address will not be the same. For this it is important to know that the "determining" part of a URL address is the last one before the first slash. For example, in the address
After "https://" (which is the protocol indication for the browser) comes a block of text ending in slash ("/"), that is the address (hive.blog), but if there are several dots in that block of text, the domain is determined by the last part.
For example, if I have https://whatever.domain.you.want.net/index.html, the real domain of that site is "want.net", what is after the slash is the specific page to access, and everything that precedes want.net corresponds to subdomains, something that also serves to create scripts, as in the case of https://images.hive.blog that is the part that is in charge of processing the images of Hive.
This explanation is important to understand that if we enter in a web site that has as URL https://hive.blog.otherdomain.io/login.html although there appears "hive.blog" we are not in Hive but in "otherdomain.io" and if it presents us the Hive login form and we put our data, we will have given them our access key.
By the way, this recommendation applies not only to Hive, as this is the main way in which account thieves obtain bank account data and much more.
Therefore, our first precaution to prevent someone from obtaining our passwords is to verify that the pages where we place them really correspond to the Hive platform.
How? by always checking the URL address
Prevention
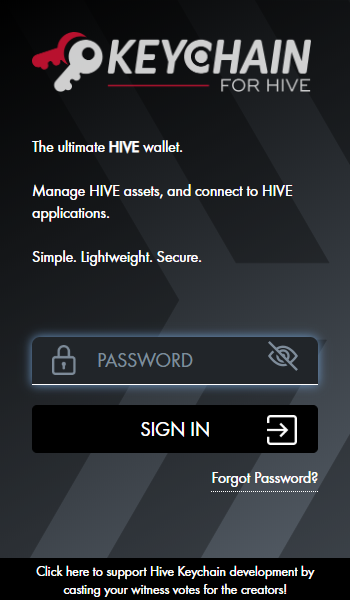
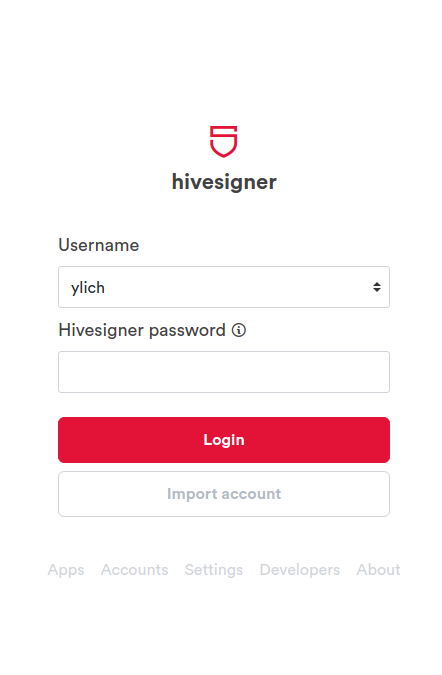
I recommend all users to use key managers such as Hive Keychain and Hivesigner. However, this second one has the disadvantage that it requires confirmation of the operations on its website, so you must pay close attention every time it asks you for the data and make sure that the address https://hivesigner.com/ is in the address bar.
Doing a brief search in the search engine of your choice you can find posts about where to get them and how to use these two tools.
I know there are others, but these two are the ones I use and recommend.
 |  |
|---|
These two tools allow you to do all operations related to Hive and other related sites and they only store the passwords in the browser, so your keys are not at risk there. With the use of these tools you do not have to be entering your private Hive keys, but only the password that you create for them.
Edit: I wrote two posts about each of these tools
Understanding Hivesigner - Security guide
Understanding Hive Keychain - Security guide
The master key ⛔
Unfortunately, the most recent case in which I was trying to recover an account, the person was using her master key for all her operations.The moment someone else has access to that password, the main battle is lost, because if that person changes the passwords, there is no way to do almost anything.
That is why it is so important to understand that the master key should only be used to generate the keys for regular use, i.e. the posting key, the active key, the owner key and the memo key. Otherwise this one should be kept in the safest possible place and backed up alternately to avoid losing it. This is the key that can save your account in most cases and you should not use it for anything else.
To post, vote, comment and manage your additional tokens, you only need the posting key. To vote for witnesses, modify your account data and manage your funds, i.e. transfer money, Power Up or Power Down, move your savings, etc. you need the active key. In both Hive Keychain (which is my favorite) and Hivesigner, you will only register those two keys and that is enough for all your operations.
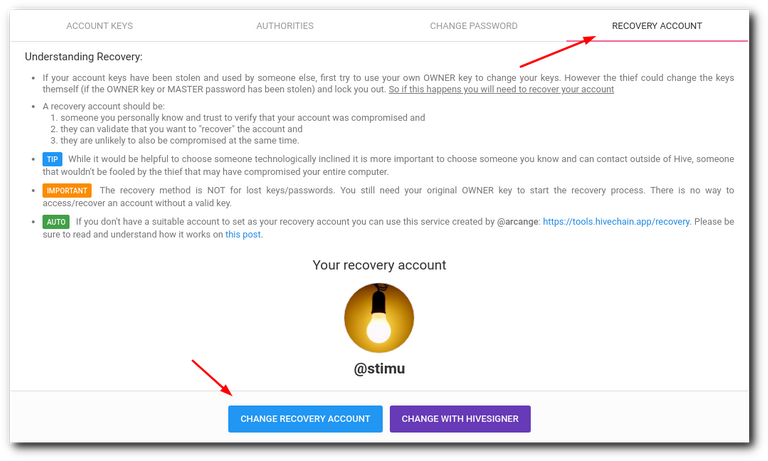
The recovery account
Since the birth of Hive, @arcange and several of the witnesses started to make a big campaign for all the people who came with accounts from Steemit, to verify and change the recovery account. By default all accounts created at that time, have as recovery account @Steem. But this account had its function in that platform, in Hive it is not active.
There is a procedure in our platform, which is not perfect or infallible, but with which you can try to recover an account, even without having the master key, but for that you need that the user indicated as "recovery account" can confirm that you are the real owner of that account. Therefore you need to place there a user who can affirm with property that it is you, because if you place, for example, @hiveio, although this account is active on our platform, they have no way to affirm who is the true owner of a given account.
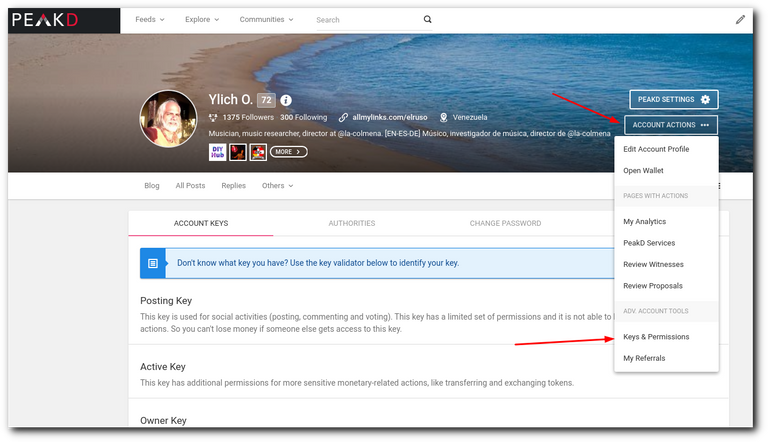
In Hiveblocks.com you can verify who appears as "recovery account", you just have to put your username instead of mine: https://hiveblocks.com/@ylich
Although there are different ways to change this information, the easiest way, in my opinion, is in Peakd.com, in "Account Actions" and there in the "Recovery Account" tab.
In conclusion
It is true that there are very complex ways for a thief to get into all computers and that there are wicked scripts capable of searching and stealing data. While it is true that a hacker with practice is able to get into your computer and see everything you have there, it is also true that this is the least common. What usually causes us to lose our accounts, is not realizing that we are giving our access data in the wrong place. And since these sites generally do not say "thank you for giving us your password and now we are going to steal your account", but usually redirect you to the page you thought you were going to access, you do not even realize when you were fooled.
Taking this into consideration, it is clear that if you start using your Hive Keychain and Hivesigner key managers; if you are aware that when a page asks you for your passwords, it really is the site you intend to enter; if you do not use your master password at all and keep it well guarded; if you place as recovery account a known person within your reach, you will most likely never lose your account, since these are the key steps for its preservation.

Via Giphy
Main image source | Screenshots made by myself

If you don't have an account at Hive yet, I invite you to read my post My Hive Testimony || Mi testimonio Hive
Si aún no tienes cuenta en Hive te invito a leer mi publicación My Hive Testimony || Mi testimonio Hive


Thanks for this helpful article.
My pleasure! 🤗
¡Hola y buen día! He notado que cada vez que entro a la página de Hive me pide antes que loguee de nuevo, pero esa ventana de inmediato se retira. Creí que era una falla del sistema, pero ahora veo que no es así.
¡Muchas gracias por compartir con nosotros tan importante información, @ylich !
He visto que en algunas computadoras se presenta esa característica. Creo.... que es como una pequeña falla, como un retraso en la detección del usuario. De todos modos, lo ideal es estar siempre alertas... 👍
¡Gracias a ti por leer y comentar!
Very good to write about this. The more people know the importance of a trustworthy recovery account the better!
I should write about it too, but it's still too fresh...
Posted using Dapplr
Excelente post @ylich
Yo soy una de las personas que tiene muchas dudas en cuanto a las claves y no se si las estoy usando bien. No se a quien preguntarle, por eso al leer este post le explico y agradezco de antemano su orientación con las mismas:
No se cual es la clave maestra.
Tengo un usuario y contraseña que me dieron cuando me inscribí.
Actualmente estoy usando ese usuario y contraseña para entrar y publicar, votar, comentar.
¿QUÉ HAGO? ¿ME EQUIVOQUÉ?
¿CÓMO PUEDO CORREGIR ESE ERROR?
En mi caso siempre uso peakd por la facilidad para escribir.
Luego tengo adicionalmente las claves privadas: propietario, activo, publicación, nota.
En estos momentos no se si cometí errores al usarlas indiferentemente porque quise hacer delegación de hp y me dice error.
¿Cómo coloco a una persona conocida para recuperación?
¡Mucho agradecería su orientación!
¡Muchas gracias!