New feature: detection of malicious code in blocks [XSS, SQL INJECTION, CSRF]

src
In the past few weeks I found some XSS vulnerabilities in some Hive tools.
After reporting them to witnesses and devs that maintained those apps, I decided it would be helpful to add to @keys-defender's list of weapons the ability to timely detect potential code injection attempts. This should mitigate the issue of attackers targeting the Hive ecosystem of apps and tools.
This bot now uses the following to try to detect potential malicious code published in blocks:
~300 fragments of code for XSS (Cross Site Scripting)
~50 fragments of code for SQL injections
~20 fragments of code for CSRF (Cross Site Request Forgery)
~ ...
These dictionaries will grow in size and be adjusted based on false positives.
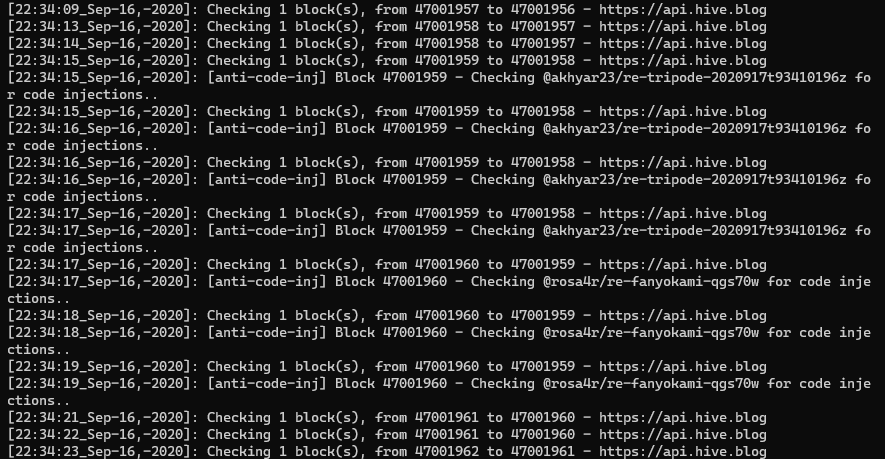
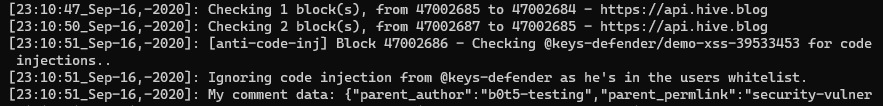
If the code injection is attempted in a post or comment (eg. this test comment of mine), the author will now receive an immediate reply from this bot:
Logs for code injection checks
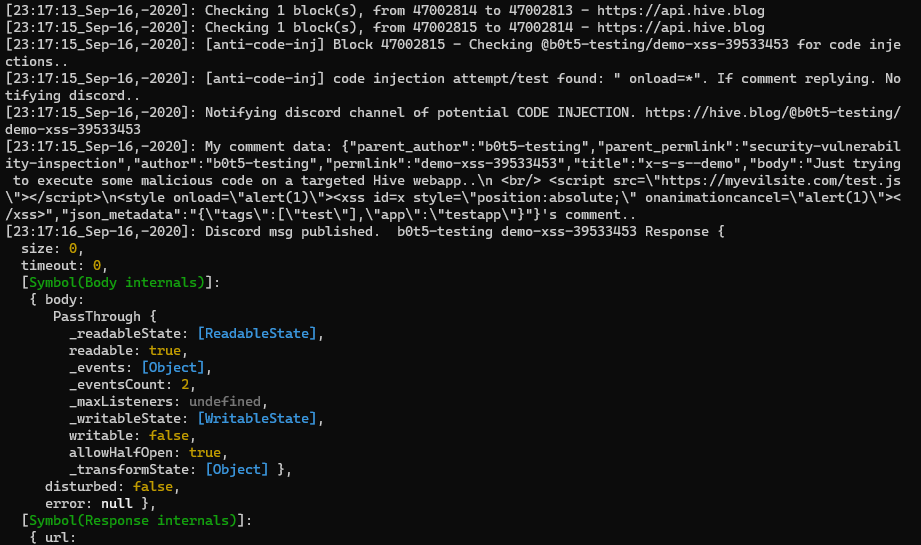
Example of @keys-defender's reply
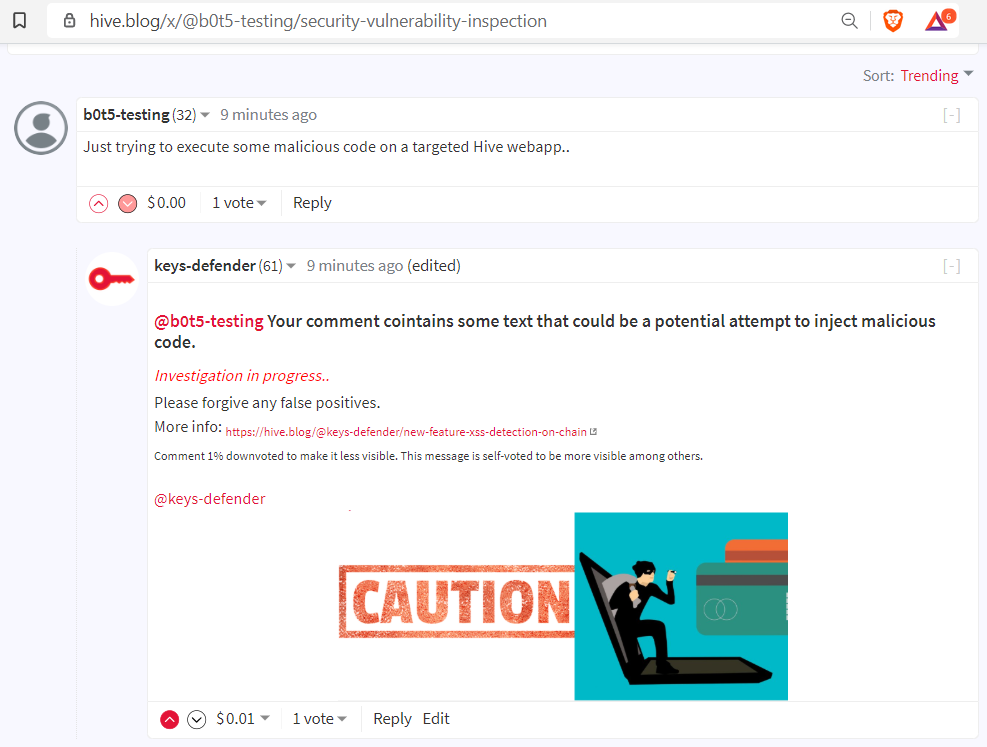
A notification is also immediately sent to my Discord server so that I or witnesses and volunteers in it can investigate and react accordingly to report and fix the targeted website or tool.
Clearly if a bad actor was indeed trying to compromise a website, their account name would also been known because, as per the blockchain design, past blocks cannot be edited or deleted.
Discord notification example
A whitelist is also in use so that known Hive apps devs like @louis88 won't be bothered while testing dapps for vulnerabilities.
Stay tuned for more updates and please feel free to suggest new features and improvements! 😎
- Introductory post for @keys-defender launch
- Automatic-posts on leak detection, weekly reports
Other features:
- Phishing protection
- Re-posting detection
- XSS vulnerabilities in scribe.hivekings.com
- XSS vulnerabilities in hiveblockexplorer.com
- Malicious ads redirecting all Steemit iOS users to a phishing site
- Reverse tabnabbing and clickjacking in steem.chat and steeemit registration page
- Curation trail
Follow @keys-defender's curation trail to upvote all its posts with a fixed vote weight. HOW: search "keys-defender" on Hive.Vote: https://hive.vote/dash.php?trail=keys-defender&i=1
I think this update might be getting false positives with Vimm Livestreams, just had a VoD replay post get a notification about malicious code from y'all.
Edit: Devs whitelisted Vimm, all is good. Thanks, mates.
@badpupper I now whitelisted vimm.com.
Thanks for notifying me and apologies for the disturbance. 🙂👍
!discovery 30
This post was shared and voted inside the discord by the curators team of discovery-it
Join our community! hive-193212
Discovery-it is also a Witness, vote for us here
Delegate to us for passive income. Check our 80% fee-back Program
If feeling_nasty then
do_bad_stuff_and_steal_keys
Will it pick that up :) This is good work as there will be bad actors out there. I would hope people are using things like Keychain to reduce the exposure of their keys, but many will not.
Thanks and have a !BEER
@steevc Well it looks like it didn't, you gotta be one of the good guys then 😉
It's not only about the keys this time. The purpose of this feature is to detect early attackers targeting websites and Apps in the Hive ecosystem trying to inject malicious code in blocks to see if it executes in the platform under test. It's a preventive measure that will allow us to know in a timely matter if someone is trying something funky and hopefully even discourage them too as their account name will immediately be known.
We have to be vigilant. With so much money at stake there are bound to be attacks. Thanks.
View or trade
BEER.Hey @keys-defender, here is a little bit of
BEERfrom @steevc for you. Enjoy it!Learn how to earn FREE BEER each day by staking your
BEER.Hmm is there even any reported case of using json metadata to steal keys?
@tngflx No, I'm not sure if anyone ever compromised a site/app in that way but I've seen people testing those attributes too, yes.
Eg. See louis88 (dev, good guy) testing various fields (in several frontends) including communities names and tags: hive.blog/@louis.random
And bear in mind that this bot scans every single type of operation published into Hive, not only the json metadata of posts and comments. I check for leaked keys and potential malicious code in: comment, transfer, custom_json, vote, account_create, account_witness_vote, .. you name it.
When I did find an active key in an account_update operation it taught me that some human errors will surprise you.
The highest values of saved accounts that leaked their ACTIVE keys so far are: $ ~28,000, $8,000, $1,000. :)
Yesterday you downvoted a false positive. You say it's in investigation .
Why triggering a downvote trail before beeing sure of your assumptions ?
It's wrong as it downs people's reputation.
Further more, you upvote your owncomments, which is not .... well seen by many ...
Can you please update your bot to ONLY DOWNVOTE AFTER your verification and not before?
My comment is 100% legit.
I waited 24h before posting this. I hope you will react.
solve dnow. thx