Cybersecurity: CISSP - Explaining the CIA Triad
Hello Everyone;
In one of my posts:: When Corona Ends things that I would like to pursue, I mentioned about my CISSP certification that is planned by the end of this Year - 2020. Currently, I'm doing self-reading/study and have gained a lot of exposure in the field of cybersecurity & thanks to the Official Study Guide; CISSP 8th Edition that is recommended ISC2 - SYBEX..

Since I'm preparing for the CISSP certification, I thought of sharing my understanding so that it could be helpful to other people who have an interest in Cybersecurity and plan to do the CISSP certification down the line.
I'm a strong believer in sharing knowledge and the more you share knowledge the more you get better at it. This means your concepts about the topic which you share even get better and also helps you to get other people's perspectives/points of view as to what they think about the Subject being talked about..
Hence, it's a WIN-WIN Situation..But I am not here for winning rather I just want to share my learnings during this Journey of my CISSP certification.
In this post, I talk about the CIA aka as Confidentiality, Integrity & Availablity triad.

I'll say that these are the three pillars of this CISSP certification. What I'm observing is that all topics go back to relating the CIA triangle and also this is the first topic in the book that is covered and you can simply think of CID as a security principle/essential that is a must for any organization that is looking to secure their businesses.
Think of it in this way::

A business needs to protect its DATA i.e. their data must be secure
A business needs to ensure that it's DATA doesn't set compromised and need to ensure the reliability of the data by restricting unauthorized access and implementing other security controls
Finally, the Business needs to ensure that their DATA is available all the time - which means authorized people are able to access the data without any interruptions.
Now that I've laid down some background around How critical DATA is for any Business to grow. Let's quickly look into the CIA; Confidentiality, Integrity and Availablity Triad.
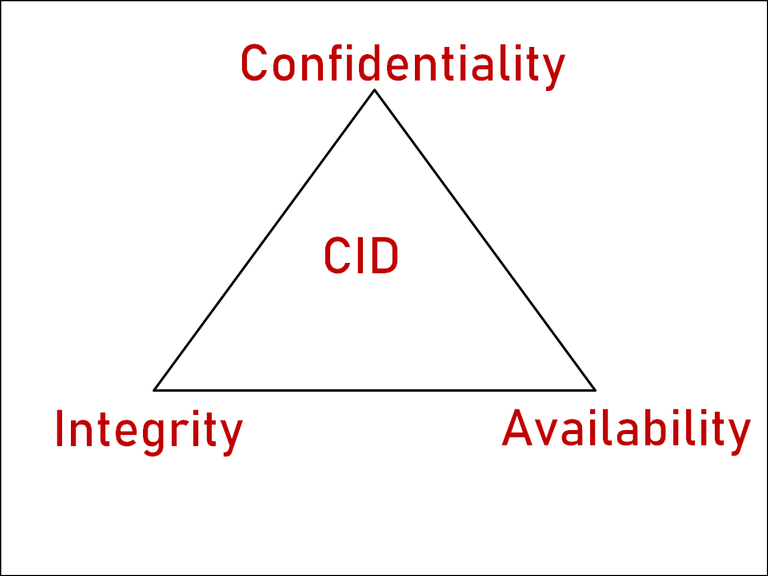
I'm not going to speak the book here but rather will example with a real-time example so that these three security pillars of any organization are understood very clearly.

Think of confidentiality as your property papers. You definitely will not want them to be lost right? Similarly big or small scale businesses or organization need to protect their trade secrets, confidential data being exchanged over the internet and many other resources which they deem is very critical for their business. There are different mechanisms that organizations adopt to protect its data like encryption, filing patients etc..but we will not get into the mechanisms of how data is protected.
But what we do need to understand is that - Confidentiality as the name suggests is all about ensuring the protection of the secrecy of data that is of utmost importance to the business.
In our example property papers are Confidential as losing them will lead you into serious trouble. And the same is true for Organizations if they happen to lose their confidential data to hackers then they would be inviting heft losses..Millions of Dollars would be at stake.

Integrity - being the second pillar of the CIA Triad talks more about DATA being correct i.e. how reliable is the data. Intergity basically ensures that the data always remain correct for most of the time, unaltered by unauthorized access and is preserved appropriately.
Let's understand Integrity with a life example::

Imagine for a moment that you plan to buy some good from an online portal. Your cart total says $500. For some reason, you didn't buy that particular day and you thought that you will buy it some other day. After some days you revisit the cart and was shocked to see the price $1000..It's obvious that you won't buy with such a huge difference..But what we can infer with this spike in price is that something has gone wrong at web portal end selling the product and possibly could be an hack of the website where the hackers are trying to defame the reputation of the organization selling the products.
So in this example this is a clear case of Organizations Integretity being compromised wherein unauthorized access to data have to lead to all those changes of price on the portal..Hence Integreity is considered to be one of the important principles of Cybersecurity..

Availability - is all about making sure that the DATA is available all the time for use. Imagine your email provider service is down most of the time..You definitely will want to change your Email Service Provider coz. it's down for most of the time..
Take another example of a blockchain technology that you leverage to post your articles online. You were almost done with writing your article and ready to post it but found that the blockchain service is down and isn't available for you to post the article. How frustrating it gets. I can imagine. coz. of this reason for unavailability, you plan to move to HIVE blockchain where it claims its Uptime is 99.99% this makes you feel happy and you decide on to move to HIVE blockchain.
Similarly, on those lines of the example stated above - you can imagine how critical it is for Business to maintain/provide the data availability for almost all the time; else you know the consequences that customer won't give it a second thought and will plan on to move to other competitors providing similar services..
I, hope I was able to explain the CIA Triad and if you have any questions around it, please feel free to use the comment box to list down your doubts/questions. I'll try answering them to the best of my ability.
A final note on CIA Triad; every organization have unique set of security requirements. But the goal is the same as securing DATA at all times. If you can correlate things that are tied to confidentiality, integrity, and availability then I am sure you would have understood the CIA Triad perfectly..
Best Regards..
Resteemed already. Upvote on the way :)
@tipu curate
Upvoted 👌 (Mana: 14/28)
He said, 'Stop doing wrong things and turn back to God! The kingdom of heaven is almost here.'(Matthew 3:2)
Question from the Bible, What are God's guidelines for us to become righteous? [Part 1 of 3]
Watch the Video below to know the Answer...
(Sorry for sending this comment. We are not looking for our self profit, our intentions is to preach the words of God in any means possible.)
Comment what you understand of our Youtube Video to receive our full votes. We have 30,000 #HivePower, It's our little way to Thank you, our beloved friend.
Check our Discord Chat
Join our Official Community: https://peakd.com/c/hive-182074/created
Can you refer me to some genuine resources where I can delve more into Cyber Security? It's really interesting. Any pdf if available that will be great because online resources very often have intruding ads, which makes the overall reading experience very poor. Thank you.
Based on my experience, I also tried reading stuff on the internet but the problem is that you don't get organized and don't know how which topics to read. If you are planning for the CISSP certification then go for the SYBEX book I mentioned..that is highly recommended.
Also, check https://www.pdfdrive.com/ you can get many ebooks tied to any subject here.
Thank you so much for the info.