My Writeup for BCACTF 2.0! (Forencis Problem #2 and Forensics Problem #5: Password Cracker)
Well this is my last writeup for BCACTF 2.0. In total I got 900 Points and placed myself at Rank 393 out of 966 participants. It's actually not that bad for a 1-man-team who only participated for 5-6 hours (Heh excuses!). XD
Anyways, for this post I would share my write-up or walkthrough on Forensics Prolem #2 and #5.
Forensics Problem #2: Zstegosaurus
My friend forgot our pet zstegosaurus's name. Luckily for him, I hid the dinosaur's name somewhere in this picture...but now I can't find it. Can you help us?
zstegosaurus.png
Hint 1 of 3: The image should be black and white...right?
Hint 2 of 3: Try opening the file in a hex editor.
Hint 3 of 3: The format for the flag is bcactf{flagName}
My Approach/Solution:
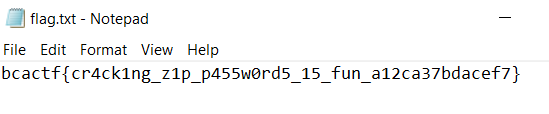
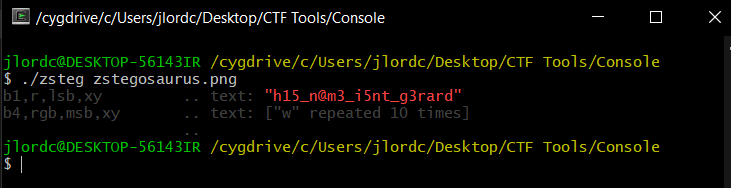
Well even without opening the Image File above (which contains a veryyy simple drawing of a dinosaur by the way) and even without looking at the 3 HINTS, the first thing that pop into my mind was just to use EXIF on the .PNG file above.
And so I did, and VOILA!!! Found our flag in less than a minute!!! The Flag is bcactf{h15_n@m3_i5nt_g3rard}
Forensics Problem #5: Secure Zip
Gerald lost his homework in this zip file. He needs to extract his homework or else he fails CTF101.
chall.zip
Hint 1 of 2: A quick google search of "Free/Fast Zip password cracker" will help find the right command
Hint 2 of 2: Gerald loves listening to the song that goes "we will, we will".
My Approach/Solution
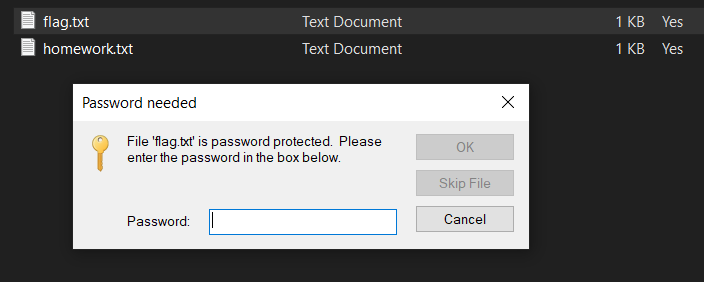
Downloading the Challenge ZIP File above gives us a .ZIP file that contains two .TXT files namely FLAG.TXT and HOMEWORK.TXT.
The Problem is (or the Challenge in this case) is that it is PASSWORD PROTECTED. So the pretty straight-forward approach to this challenge is just to simply crack what the password is. XD
After reading the HINT above, I Google searched it and it somehow gave me a password cracker called FCRACK. But long story short FCRACK did not work.
Well it would probably work but when I tried it, it was 'brute-forcing' the challenge file. Who knows how long it would take on getting the password for the challenge file above.
And so I returned back to using a password cracker I am already familiar with and that is JOHNTHERIPPER.
If you guys don't know how to use JOHNTHERIPPER well it's kinda simple. First you just have to:
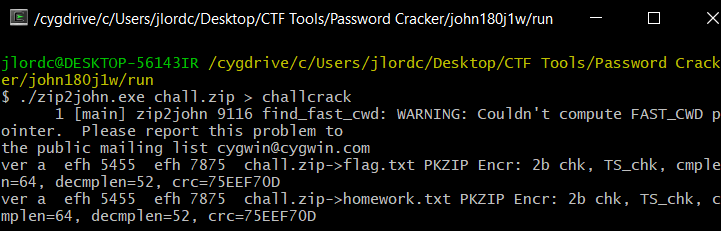
zip2john [FILE YOU WANT TO FIND THE PASSWORD] > [OUTPUT FILE]
Next is the mode. JOHNTHERIPPER also has a brute-forcing mode but judging by the hint #2 above "Gerald loves listening to the song that goes "we will, we will".", it seems that the challenge author wants us to you the "rockyou.txt" wordlist for this.
It did took me some time to figure this one out as my JOHNTHERIPPER executable is the very OLD one I used years ago and so it lacks a lot of built-in wordlists. I think the new one's have this rockyou.txt as one of the built-in wordlists.
Anyways here is how you do it (if you want to use a wordlist):
john.exe [OUTPUT FILE FROM BEFORE] --wordlist=[location of the wordlist]
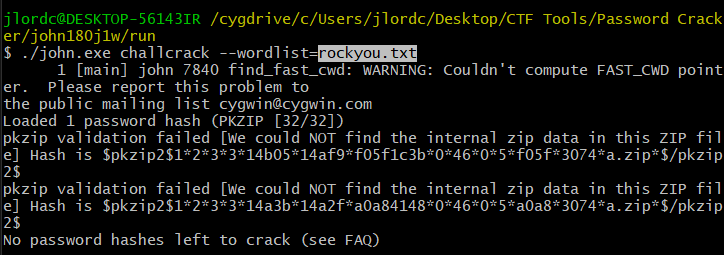
And the last one is to 'show' the cracked password.
john.exe [OUTPUT FILE FROM BEFORE] --show
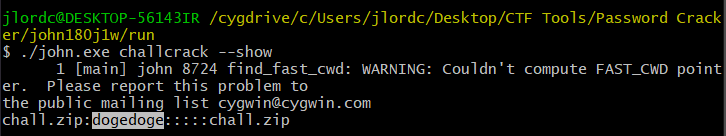
As you can see above, the password for the .TXT files above is "dogedoge".
Using the password we found above to open FLAG.txt and VOILA!!! We get another FLAG. XD