Is The Passphrase For Your Hardware Wallet Strong Enough?

Using a hardware wallet is an extra layer of security for your cryptocurrency keys. These devices store your keys and instead of entering them into soft wallets, websites or apps, you connect these hardware wallets to your computer or mobile phone and sign any transaction directly on the device. Theoretically, the keys never leave the hardware wallet. They are protected by a recovery seed and a PIN - and additionally by a passphrase if you choose so.
After reading this great and important article by @themarkymark about Why you should be using a passphrase with a hardware wallet, I wanted to add some thoughts to the topic and discuss why it makes sense to use a strong passphrase.
I am no expert in this topic and just recently started using a hardware wallet myself. Please do your own research on top of this and make sure you fully understand all the implications of using a passphrase.

What Are The Recovery Seed & PIN?
Before we come to the point of this article, I quickly want to explain the concept of the recovery seed and the pin. In case you loose or break your hardware wallet, it has three layers of protection to keep it safe from others and to restore your keys to another device or soft wallet: the recovery seed, the PIN and the passphrase.
The recovery seed is a 12 or 24 word long string, that encodes the content of your hardware wallet. With this seed, you are able to restore your hardware wallet to the same or another hardware wallet (or even use multiple hardware wallets with the same keys) or import your keys to a desktop/mobile app that supports this technology (which potentially puts your keys at risk by compromising them, so only do that as the very last resort). If you are using the browser extension Meta Mask, you already have used a similar recovery seed encrypting your Meta Mask wallets.
The PIN is a one to nine digit long number, that you can enter into your hardware wallet and change at any time. It will give access to your device whenever you connect it to a computer or mobile phone. This is protection for your device itself, in case it gets stolen or you loose it.
However, apparently it is possible to extract both the recovery seed and the PIN from your device, IF the attacker gets access to the physical hardware wallet and has the technical know-how to do so. Over time, this will become even easier, as technology advances. In order to add yet another layer of security to your keys, the so-called passphrase comes in.

What Is A Passphrase?
Trezor has created a great video, that briefly explains what a passphrase is and how it gives you access to unlimited wallets within your device, every time you enter a different passphrase. In short, it is basically another password in form of one or several words, alphanumerics and ASCII symbols, that you can choose yourself and which are NOT stored on your device and hence cannot be extracted from it. This makes it super secure (but also risky, because you might loose or forget your passphrase and forever loose access to your keys and funds).
This brings me finally to the point of this article: what exactly is a strong passphrase?

A Strong Passphrase
Since we already know that any hardware wallet is at risk to get its recovery seed and PIN extracted, then we have to prepare ourselves accordingly for this worst case scenario and assume, that the recovery seed and PIN are automatically compromised when our device is stolen or lost (which obviously is not automatically the case but COULD be the case).
This means, that the person who gets access to your device would then begin with a brute-force attack on your passphrase.
In cryptography, a brute-force attack consists of an attacker submitting many passwords or passphrases with the hope of eventually guessing a combination correctly. The attacker systematically checks all possible passwords and passphrases until the correct one is found. Alternatively, the attacker can attempt to guess the key which is typically created from the password using a key derivation function. This is known as an exhaustive key search.
Of course, nowadays this brute-force attack would happen automatically with services like Amazon Web Services (AWS), allowing you to do millions of computations per second for very low cost. Trezor has a very informative article about this whole topic of how secure your passphrase is:
Link: Is your passphrase strong enough?
Here we get examples of how much it costs to crack a passphrase in average, using AWS to create a brute-force attack, both today and in the year 2030, where computational power has grown and costs are lower.
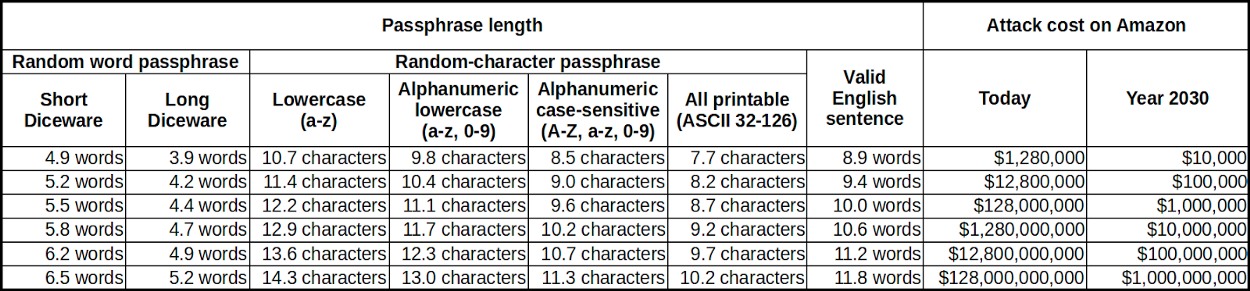
There are multiple approaches listed of how to create your passphrase, that I will not go deeper into in this article (the Trezor article goes into full detail and I strongly suggest you give it a full read). All of those methods assume a maximum entropy, meaning random passphrases, not something you picked manually, except for the English sentence approach (here it is suggested not to just use some popular poem for example but ideally something you came up with yourself).
As you can see, it costs 1.3 million USD in average to crack any of the top row examples, like 3.9 words of the long diceware list or 7.7 characters of all printable ASCII signs. That is very expensive but would already be worth the effort, if the attacker expects at least twice of that amount being held on your hardware wallets keys (twice, because the costs are an average estimation and it might take longer to crack and hence is more expensive). In 2030, the same passphrase would cost only 10,000 USD to crack due to the lower costs and greater power.
If you only have a few thousand USD worth of cryptos on your device, you might be fine with a short passphrase, even in the year 2030. Just one single word is already a great extra protection and you probably never need anything stronger than that. But the more you are planning to store on it, the longer or rather more complex your passphrase should become. Using the example table from Trezor, you get an idea what protection strength might be enough for you.

Conclusion
Creating a passphrase for your hardware wallet is an extra layer of security and something you should really consider to use. Why would you invest money into such a device in the first place, if you are not using all its available security measures?
Now, there are certainly arguments against a passphrase, like the greater responsibility on your own shoulders, to keep that passphrase safe and never loose it. Even if you still have your hardware wallet, when your passphrase is lost, your funds are lost. Another one is that you have to enter your passphrase before signing a transaction on your device, making it a tiny bit more complicated (only once per session, as long as you keep the hardware wallet connected to your computer or mobile phone).
What probably is the most intimidating part with a passphrase is how to store and/or remember it, since you will need to enter it regularly. I will soon write about how to memorize both your recovery seed and your passphrase - no matter how long you made it - using very reliable memory techniques. This makes it super easy to access and use. Still, you might want to keep a backup of your passphrase somewhere safe. But more about that soon.

Posted Using LeoFinance Beta
It would be extremely difficult to brute force a passphrase regardless of how strong it is. To even attempt to use a passphrase you have to disconnect/reconnect the device and know the original 12/24 seed words in addition to knowing there is actually funds hidden in some unknown passphrase.
The only advantage is the device won't self destruct after three failed attempts like the PIN because there is no such thing as a "wrong" passphrase as any passphrase can be paired with a set of seed words.
Posted Using LeoFinance Beta
True, if the attack would go against the device itself. But in my example we already assume that the recovery seed and PIN have been extracted from the device and now the hardware wallet has become useless and would not be further required for an attack. From this point forward, you can simply access the content with any compatible wallet or even write it yourself and there you have no device lock protection that would slow down the brute-force attack.
Trezor writes in the article linked above:
This leads to the calculation table with the average costs for cracking the passphrase.
I have nightmares about kicking the bucket and picturing my wife trying to figure out all of the accounts and wallets I have! There will come a day when my stake is big enough for me to take care of it properly like this.
Storing keys becomes a security risk so it really is a balancing act.
Congratulations @flauwy! You have completed the following achievement on the Hive blockchain and have been rewarded with new badge(s) :
Your next target is to reach 1000 posts.
You can view your badges on your board and compare yourself to others in the Ranking
If you no longer want to receive notifications, reply to this comment with the word
STOPCheck out the last post from @hivebuzz: